Table of Contents
- Amplification Methods in Stresser Services
- Exploring Booter Services
- Grabify Tools and Their Impact
- IP Stresser Use Cases
- The Role of IP Stressers
- IP Grabbers and Their Usage
Amplification Methods in Stresser Services

NTP protocol boosts is a widely used
technique in stress testing, especially for large servers. It maximizes attack efficiency
while increasing traffic load, challenging network stability in a controlled environment.
- DNS amplification
- NTP boost method
- CLDAP traffic magnification
Exploring Booter Services

Booter services are crucial for enterprises
testing load limits. These tools allow for controlled stress tests
on targeted infrastructure, making them ideal for comprehensive security assessments.
Grabify Tools and Their Impact

Grabify solutions provide real-time insights, empowering organizations
to track and respond to unauthorized access attempts effectively.
IP Stresser Use Cases
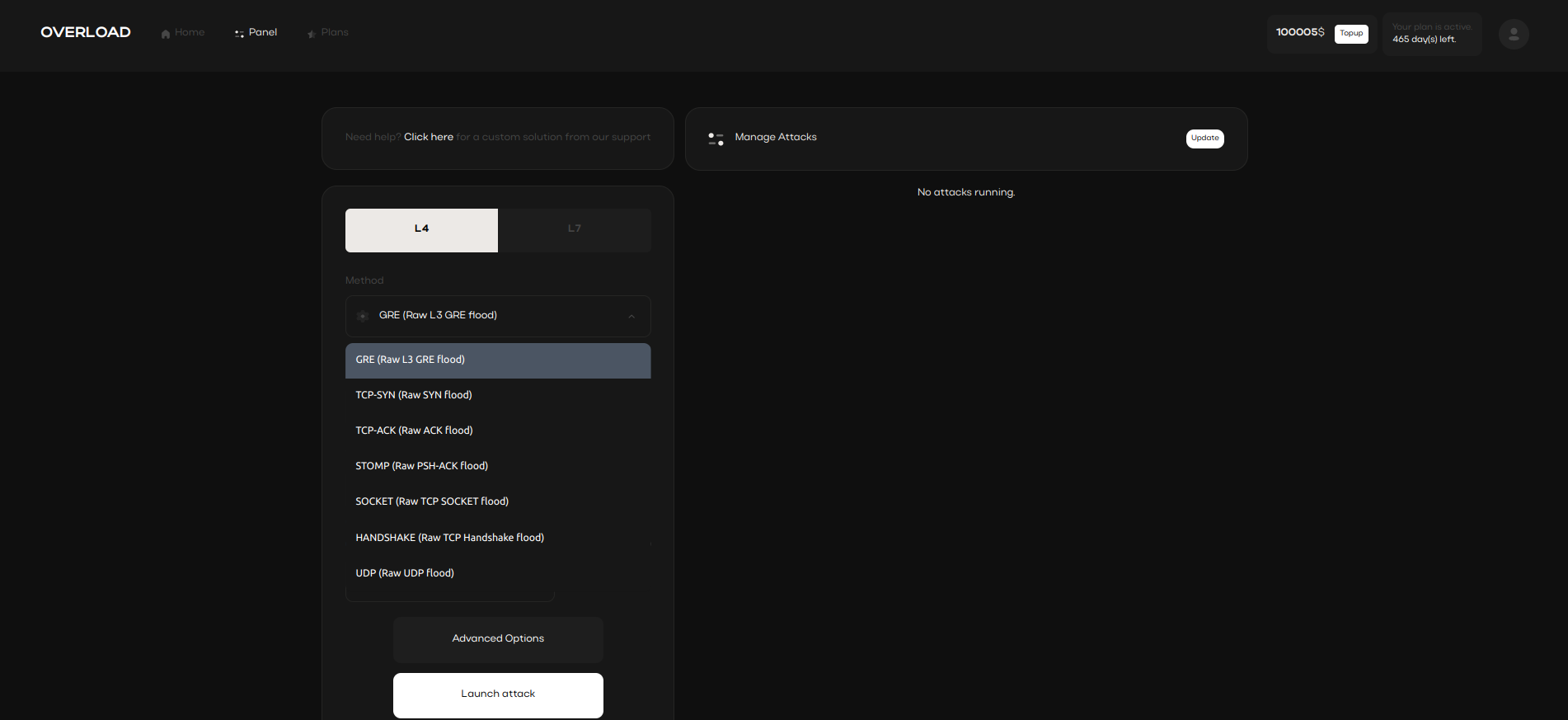
IP stressers are invaluable for organizations aiming to simulate high-traffic scenarios.
These tools highlight system vulnerabilities, helping businesses implement effective safeguards.
The Role of IP Stressers

IP stressers are valuable tools for testing network robustness.
By simulating high-traffic scenarios, they help identify potential vulnerabilities
and ensure server stability under stress.
IP Grabbers and Their Usage

IP grabbers are effective tools for extracting and analyzing network data.
They support cybersecurity efforts by identifying potential threats
and monitoring unusual activity.
ddos stresser
ip stresser
xresolver
booter
stresser ip
dream stresser
stressthem
xyz booter
vps for ddos
stresser tool
buy ddos attack service
boot ip address free
quez in
booter ip
buy ddos attack
stark stresser
dark stresser
l7 stresser
ipfighter
stresser ai
buy ddos
stresserlab
cryptostresser com
buy ddos attack
quez in
booter panel
ddos attack service
botnet ddos
ip booter download
ddos master
mhddos
stresser ddos fivem
5 min booter
ddos master
stressers
bot protection cloudflare
ddos attack in cyber security

